This is part III of our cyber security blog series. Here we cover what is considered a Conventional Threat.
For decades, we’ve all become familiar with the ways we protect from viruses, spam, adware, trojans, and other malware we refer to as conventional threats. Comparative to new threats like phishing and ransomware, conventional threats are generally known and understood.
Conventional threats have a signature, or a way to identify it by the files or breadcrumbs they leave. the protection tools we all use – like spam filters, firewalls, and antivirus – are given the keys to how to find, block, and clean conventional threats.
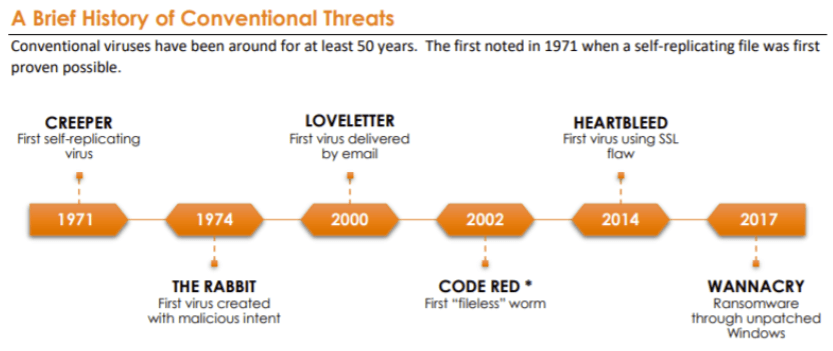
Every day, at least 560,000 instances of new viruses, malware, or spam are created and set loose upon the World Wide Web. Firewall rules, spam filters, and antivirus definitions are updated to protect from the new malicious code. In the lifecycle of a conventional threat, new malicious code is released, security professionals become aware of it, the threat is decoded, and the security software is updated to detect and stop it in the future.
The time when a conventional threat is most dangerous is in its early stages of creation before detection instructions are known, and security solutions have not yet been updated with the keys to detect and prevent. Without the instructions, antivirus/spam filters/firewalls do not have enough information to identify the risk.
While attacks are orchestrated under the guise of many names, there are ways to shield yourself from potential ruin. With the general adoption and maintenance of defenses like firewalls, antivirus, antimalware, spam filters, a virtual private network (VPN), connections, and encryption, these types of attacks are kept at bay.
These conventional defense approaches work because the threats are detected, studied, and understood. They rely on the understanding of how each attack works and where they come from, learning the signature of each, and updating the protection tool with rules to detect and remove the threat.
Our Advanced Threat Protection security service is a premier security service built to stamp out growing danger. Take the first step towards securing your company’s delicate data by calling us today!
Stay tuned for the upcoming article Part IV: Next Generation Threats.
